

A process is "a program in execution." It has an address space, and a set of resources to which it has access, such as files, registers, related processes, and more, and other program information. A process is the set of all of this information necessary to run a program.
While I am lecturing, your laptop has several processes running: you have an editor in which your are ostensibly taking notes on my lecture, your Facebook page, in which your are posting pictures of your winter break, and a chat window, in which you are typing to your (possible) significant other. The operating system must keep each of these processes running, as well as background processes that might be fetching emails, or upgrading your word processor.
The operating system provides calls that deal with the creation and termination of processes. Generally, a new process is created as a sub-process of an existing one.

Processes are associated with particular users who started them, and with groups the user belongs to. There is often a specially privileged user: in UNIX, it is the superuser, and in Windows, the administrator. In The Matrix, he is called Neo.
Two purposes:
The file system hides the messiness of disk, CD, cloud drive, memory stick, etc. details from the application programs: they can just write and read files from a location in the file system hirarchy.
A good file system allows mounting of devices at a certain point in the directory structure. So, for instance, a memory stick could be mounted as /memstick. Furthermore, special files can be mounted at places in the file system to allow programs to treat printers, modems, and other devices as files.
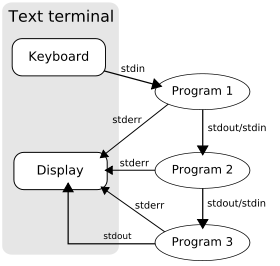
Finally, pipes are a sort of pseudo-file, used to connect the output of one program to the input of another.
Obviously, it is vital that computers be able to accept input from humans and show humans their output. Some of this can be dealt with by files, as above. But in many cases, as with a graphical display or a mouse, files are not a good abstraction for dealing with these devices. Operating systems provide services like device drivers to deal with these situations.
People often want to protect the information they put on computers from competitors, foreign governments, Russian hackers, disgruntled ex-spouses, their boss, and so on. Operating systems typically provide some form of protection.
Simple example: UNIX protection sets owner, group
and other read, write, and execute bits on every file. For
example:
rwxr-xr--
means that the owner of the file can read, write and
execute (run) it, the owner's group members can read an
execute it, and all other system users can only read it.

Happy and you know it. MS-DOS emulator
Frankly, I think the authors could have done without the Darwinian reference here, since this principle has been abandoned in modern biology. But their point that computer technologies may be "dead" at one point in time but "alive" at another is sound. They give the example of CPU caches: so long as the on-board CPU memory can be accessed much faster than RAM, we will have caches. If RAM technology speeds up significantly, they may disappear. But if the CPU jumps ahead again, they will make a comeback. It is important to understand history, and why certain concepts fell out of favor, and why they might come back into favor.
Most powerful computer in the early 1960s had 128K of RAM. The history of RAM was recapitulated on the first minis, and then again on the first micros.
The first mainframes had no protection hardware. Then
it was added.
The first minicomputers had no protection hardware. Then
it was added.
The first microcomputers had no protection hardware. Then
it was added.
The "wheel of reincarnation" spins fast in the computer
industry!
One directory to many back to one. (CPM)
Similarly, virtual memory first appeared on mainframes, later on minis, and finally on micros.
"In these developments, we see ideas invented in one context and later thrown out when the context changes... Only to reappear the context often a decade later. For this reason this book we will sometimes look at ideas and algorithms that may seem dated on today's gigabyte PCs, but which may soon come back on embedded computers and smartcards."